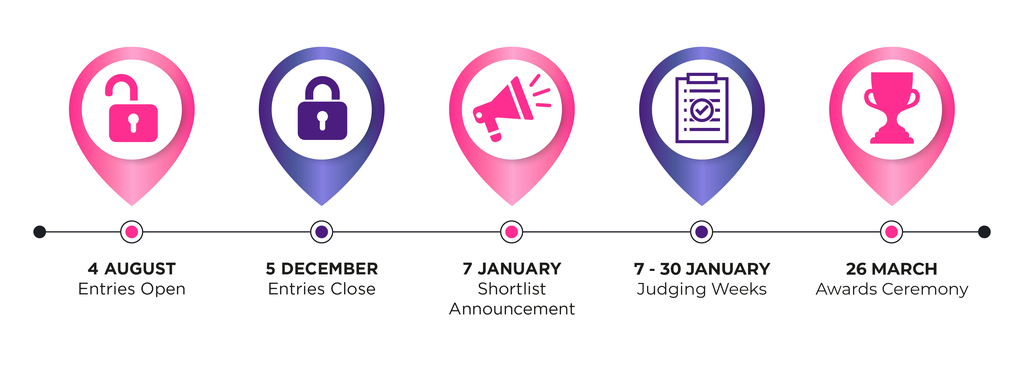
THE SHORTLIST IS NOW LIVE!
Congratulations to our finalists!
Join us at the ceremony on Thursday 26 March where we will crown our winners.
Book your table here before the deadline of Thursday 12 March. See you there!
Marking 10 Years of Recognising Cybersecurity Excellence Across the Industry
Join us on Thursday 26 March 2026 at One Moorgate Place in London to celebrate Computing's 10th edition of the Security Excellence Awards, honouring the people, products, and projects shaping the future of cybersecurity. With 19 categories to choose from, there’s a place for every achievement.
To commemorate the ten year mark, we have introduced, for this year only, two exclusive categories; the Decade of Excellence Award and the Cybersecurity Veteran Award.
Find out more about the awards here.
Take a look at our full 2025 gallery and our winners.
This could be you next!
Our 2026 Awards Partners

SUBSCRIBE TO COMPUTING FOR FREE
Receive the latest insights, news, and in-depth analysis direct to your inbox. Coverage crosses over a variety of technology areas, including cloud, cybersecurity, data centres, climate initiatives, networking, AI, software and recruitment. Plus, have first access to our podcasts with pioneers of the tech industry. Stay ahead of the competition and begin your Computing subscription today.
Contact us
